
Sandia’s nuclear facility cybersecurity risk research is focused on understanding the cybersecurity risk unique to the commercial nuclear energy sector. This research considers the use and designs of nuclear power plant safety control systems, the formal regulatory licensing process, and nuclear community stakeholder capabilities.
Nuclear Energy Security Foundational Research
Our initial research efforts included:
- survey and analysis of cybersecurity risk management practices from other industries,
- development of models and methods to prioritize and mitigate cybersecurity risks in nuclear power plant safety control systems, and
- supporting the adoption of risk-informed performance-based approaches for cybersecurity of advanced reactors.
In partnership with the Electric Power Research Institute, Sandia developed the Hazard and Consequence Analysis for Digital Systems (HAZCADS) approach to system hazards. HAZCADS is used to understand security risks at nuclear facilities and is a combination of traditional probabilistic risk assessment and Systems Theoretical Process Analysis (STPA).
Related Publications
- Cyber-Physical Risks for Advanced Reactors
- Evaluation of Joint Cyber/Safety Risk in Nuclear Power Systems
- Framework for Cyber Risk Management
- Safety and Security Defense-in-Depth for Nuclear Power Plants
- Deconstructing the Nuclear Supply Chain Cyber-Attack Surface
- Cyber-Physical Risks for Advanced Reactors
Advanced Reactor Cybersecurity by Design
To adequately plan for the future fleet of nuclear power reactors, researchers and design teams must consider digital vulnerabilities and incorporate resilience into every stage of the advanced reactor design life cycle. This process is called Cybersecurity by Design.
Under consultation with the Nuclear Regulatory Commission, Sandia researchers wrote Draft Regulatory Guide DG-5075, “Establishing Cybersecurity Program for Commercial Nuclear Plants licensed under 10 CFR Part 53.” This guide presents and demonstrates a Tiered Cybersecurity Analysis (TCA) approach that works within the reactor design lifecycle to deliver a risk-informed, performance-based approach for cybersecurity defense-in-depth.
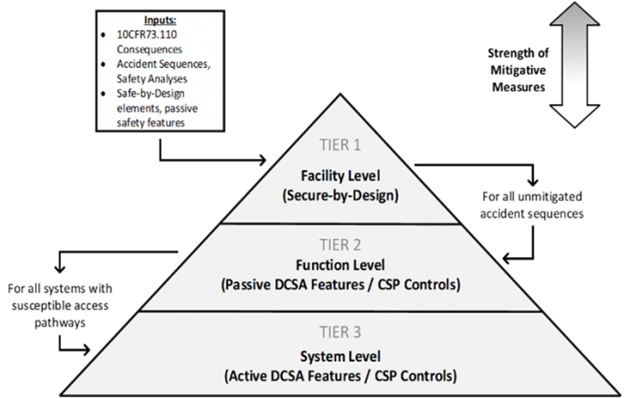
The first-tier analysis, at the facility-level, considers the digital footprint of the reactor design and consequences from plant risk and safety assessments to determine what consequences are avoided by the physis of the reactor. In the second-tier, at the function level, the intent of the analysis is to understand the adversary’s access to attack pathways that allow for the compromise of plant functions. The function-level analysis delivers cyber security plan (CSP) measures and passive or deterministic DCSA features to eliminate or control attack access. In the third-tier, at the system level, the analysis identifies protective measures including system-level cybersecurity controls to prevent or mitigate the cyber attack impact. Adversary technical sequences (ATSs) are developed with detailed attack steps to determine active CSP and DCSA implementation measures.
Related Publications
- Cyber Security Consequence Prioritized Design via Simulation
- The Sliding Scale of Cybersecurity Applied to the Cybersecurity Analysis of Advanced Reactors
- Risk-Informed Design of Defensive Cybersecurity Architectures for Digital Instrumentation and Control Systems
Modeling and Simulation
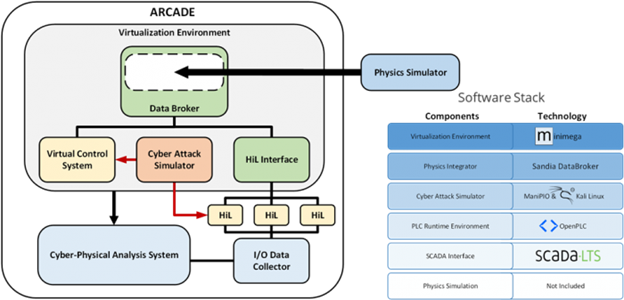
Rigorous cybersecurity analysis is critical for the design and licensing of advanced reactors using a performance-based approach. The nuclear industry makes extensive use of modeling and simulation throughout the decision process but lacks a method to incorporate cybersecurity analysis with existing models. To meet this need, the Advanced Reactor Cyber Analysis and Development Environment (ARCADE) was developed. ARCADE is a suite of publicly available tools that can be used to develop emulations of industrial control system devices and networks and integrate those emulations with physics simulators.
Impacts of ARCADE include:
- Supporting evaluation of TCA Tier 1 – supporting the confident implementation passive nuclear safety designs
- Simplifying secure-by-design (SeBD) analysis
- Evaluating Defensive Computer Security Architecture (DCSA) implementations
- Evaluating cyber-attack impacts
Related Publications
- Evaluation of Digital Twin Modeling and Simulation
- Cyber Security Consequence Prioritized Design via Simulation
Advanced Reactors Nuclear Safety Control System Design and Development
As Sandia cybersecurity research team engages the nuclear community, the need for additional research became apparent. Nuclear control system designers, already slow to evolve based on a fear of licensing uncertainty, were not keeping up with modern cybersecurity technologies and practices. Sandia resolved to remove any barriers when implementing common cybersecurity best practices in nuclear power applications. Research was also needed to prove that innovative control system concepts can be successfully incorporated into nuclear safety control system designs and defensive cybersecurity architectures. Such technologies are not new, but they are not widely adopted by nuclear control system designers due to their low technology readiness and licensing concerns.
The approach of using high integrity communication protocols is new and requires rethinking of current system designs. AR Vendors may have selected insecure protocols (e.g., HIPS custom/obfuscated, Profinet, OPC UA) and may not see the value in high integrity communications if they rely on physical system isolation as the primary security control for communication integrity.
Nuclear safety systems are important but not complex. Accordingly, several advanced reactor designers are looking to tailored implementations of Field Programmable Gate Array (FPGA)-based control systems. These designs inherently have some benefits but may not support basic Zero Trust concepts such as authentication. To address this issue, we surveyed and evaluated Secure Element (SE) technologies that can be leveraged to increase trust in digital I&C devices. The work has evolved to partnering with an advanced reactor control system designer to develop and test a secure element solution.
Related Publications
- Zero Trust Architectures in Nuclear Control Systems Report
- Advanced Reactor Operational Technology Architecture Categorization
- Barriers and Alternatives to Encryption in Critical Nuclear Systems
- Advanced Reactor Control Systems Authentication Methods and Recommendations
- Security Evaluation of Smart Cards and Secure Tokens: Benefits and Drawbacks for Reducing Supply Chain Risks of Nuclear Power Plants
- A Review of Technologies That Can Provide a “Root of Trust” for Operational Technologies
Work with Us
We partner with large and small businesses, universities, and government agencies. With multiple agreement types to select from, partners can access world-class science, engineering, experts, and infrastructure.
Contacts
Lon Dawson, ladawso@sandia.gov, Manager for Energy Security
